* Add new integration application category for Dashboard and initialize organizr service template * added images and additional info for organizr integration * alphabetized application integration categories * alphabetized integration federation and social login categories * forgot to make website-lint-fix :/ * revert mention of organizr in generic setup Signed-off-by: Jens Langhammer <jens.langhammer@beryju.org> Signed-off-by: Jens Langhammer <jens.langhammer@beryju.org> Co-authored-by: Jens Langhammer <jens.langhammer@beryju.org>
3.6 KiB
| title |
|---|
| Generic Setup |
Create User/Group
-
Create a new user account to bind with under Directory -> Users -> Create, in this example called
ldapservice.Note the DN of this user will be
cn=ldapservice,ou=users,dc=ldap,dc=goauthentik,dc=io -
Create a new group for LDAP searches. In this example
ldapsearch. Add theldapserviceuser to this new group.
:::info
Note: The default-authentication-flow validates MFA by default, and currently only Duo-based MFA devices are supported by LDAP. If you plan to use only dedicated service accounts to bind to LDAP, then you can use the default flow and skip the extra steps below and continue at Create LDAP Provider
:::
LDAP Flow
Create Custom Stages
- Create a new identification stage. Flows & Stage -> Stages -> Create
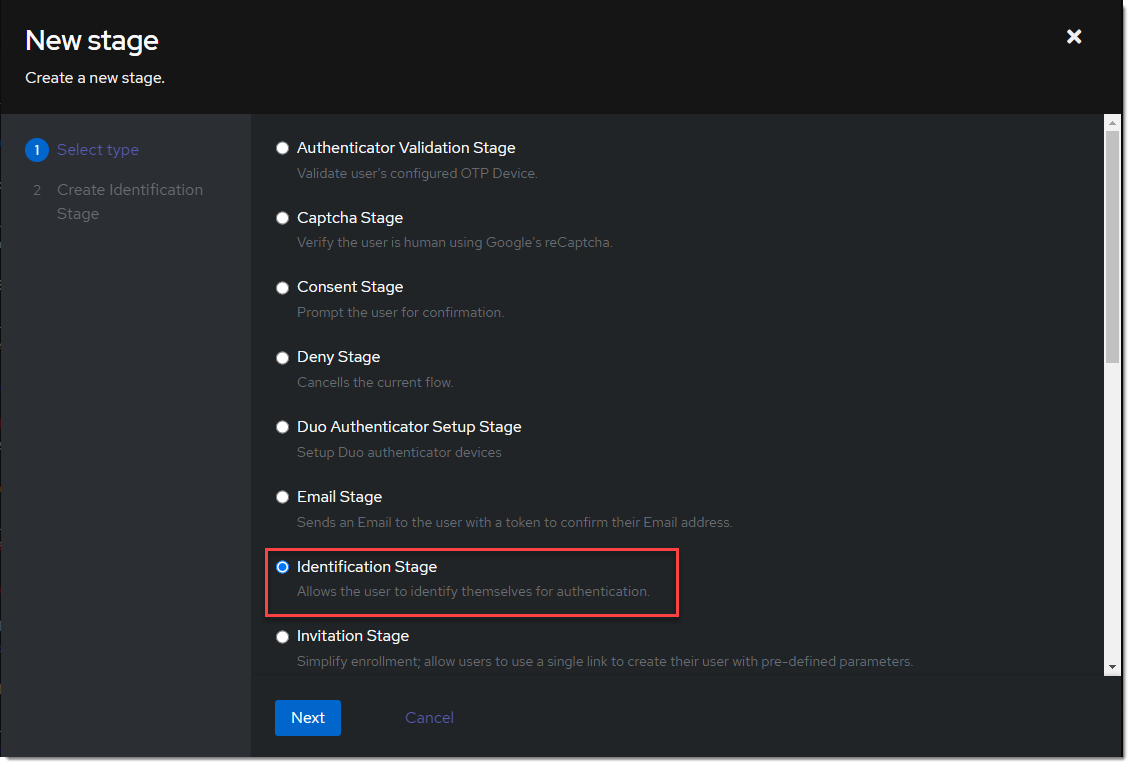
- Name it something meaningful like
ldap-identification-stage. Select User fields Username and Email (and UPN if it is relevant to your setup).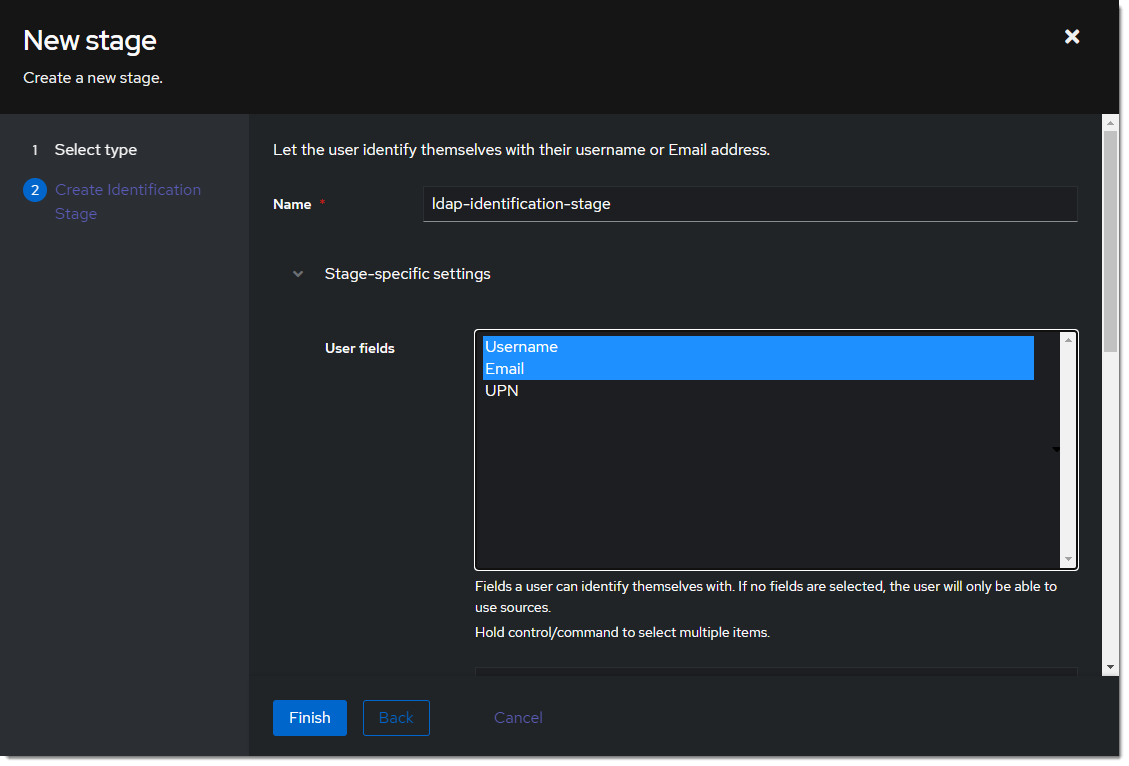
- Create a new password stage. Flows & Stage -> Stages -> Create
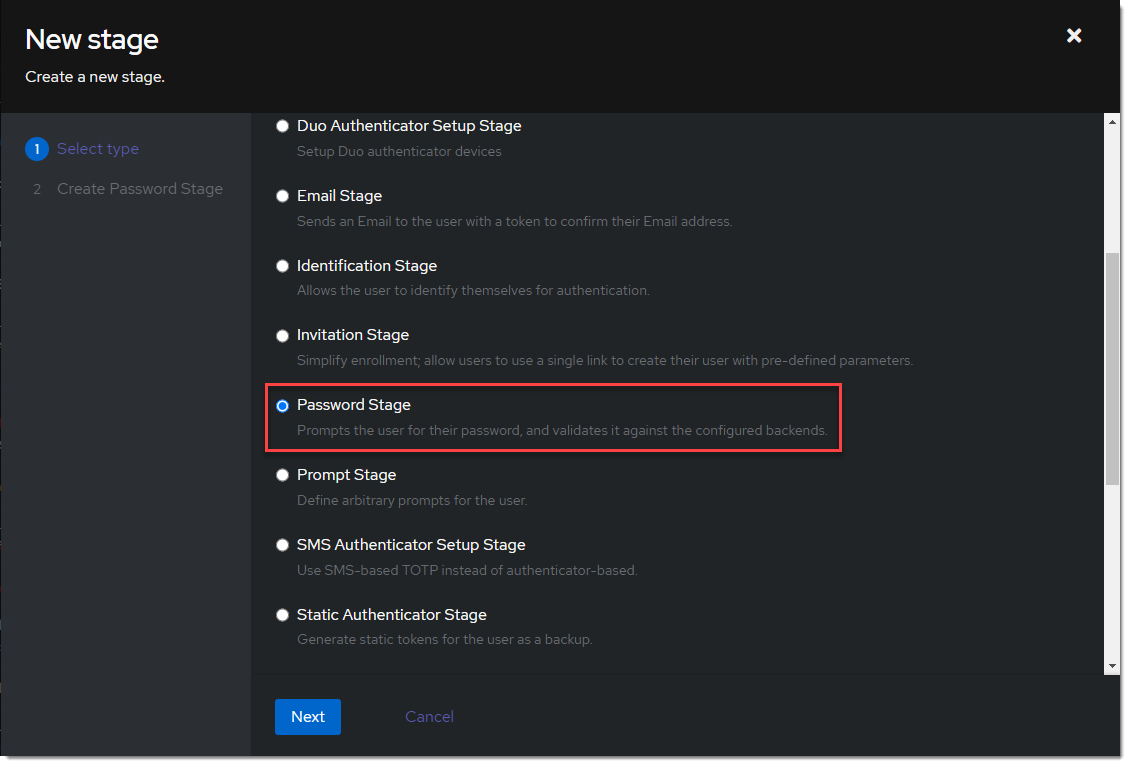
- Name it something meaningful like
ldap-authentication-password. Leave the defaults for Backends.
- Create a new user login stage. Flows & Stage -> Stages -> Create
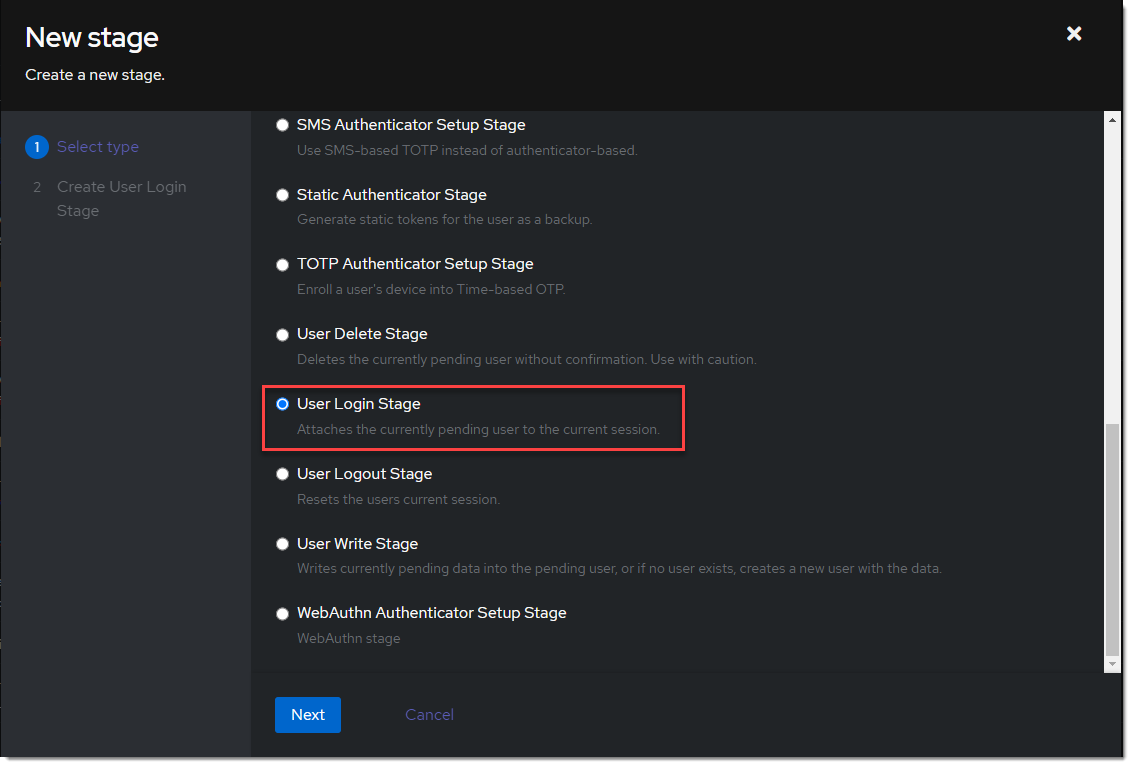
- Name it something meaningful like
ldap-authentication-login.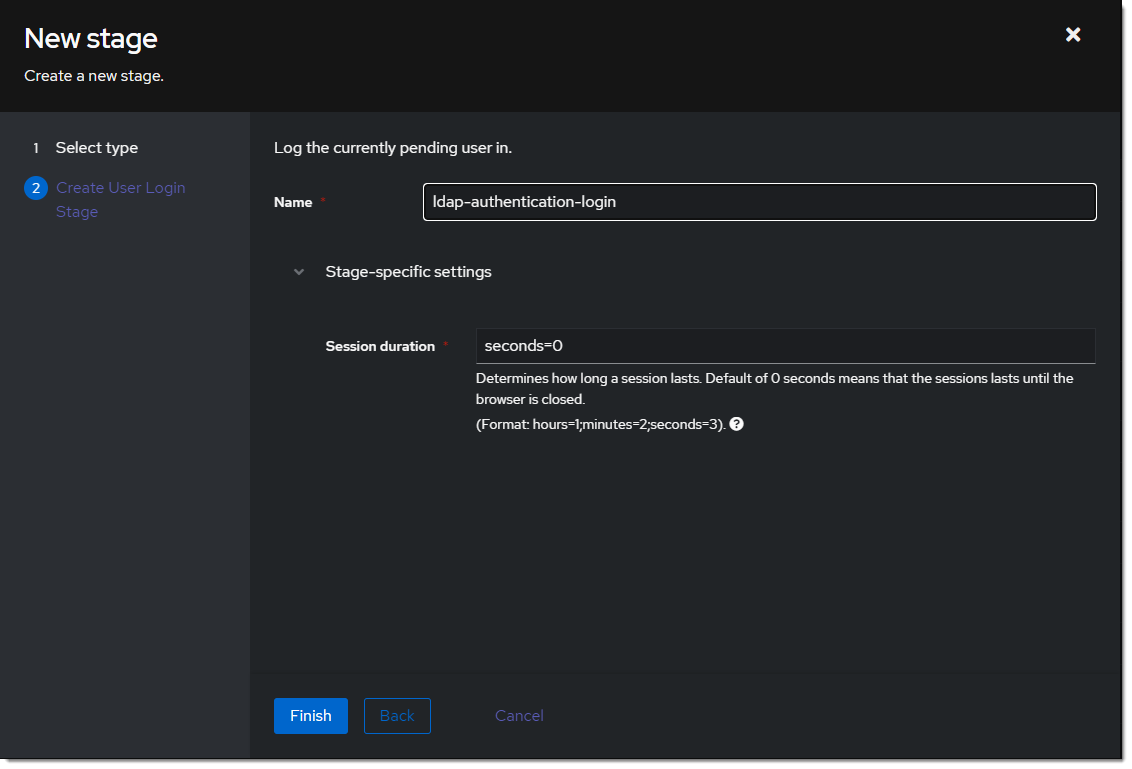
Create Custom Flow
- Create a new authentication flow under Flows & Stage -> Flows -> Create, and name it something meaningful like
ldap-authentication-flow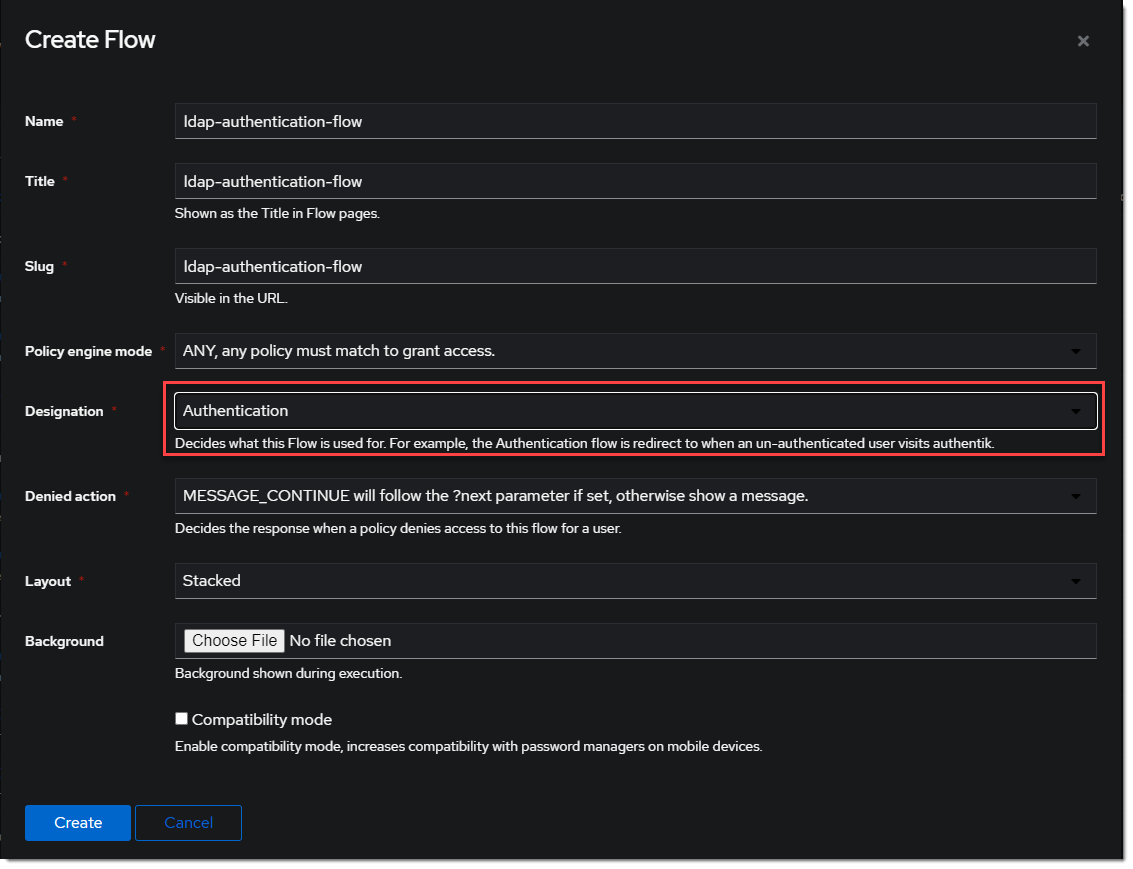
- Click the newly created flow and choose Stage Bindings.
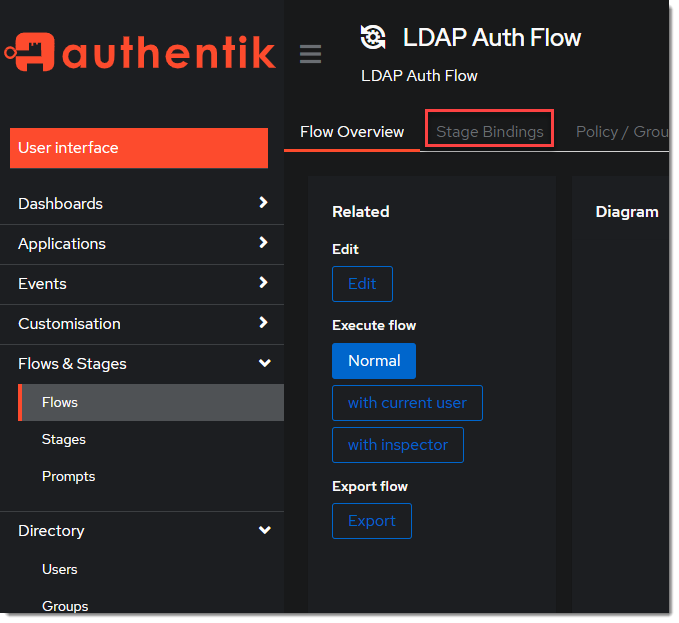
- Click
Bind Stagechooseldap-identification-stageand set the order to10.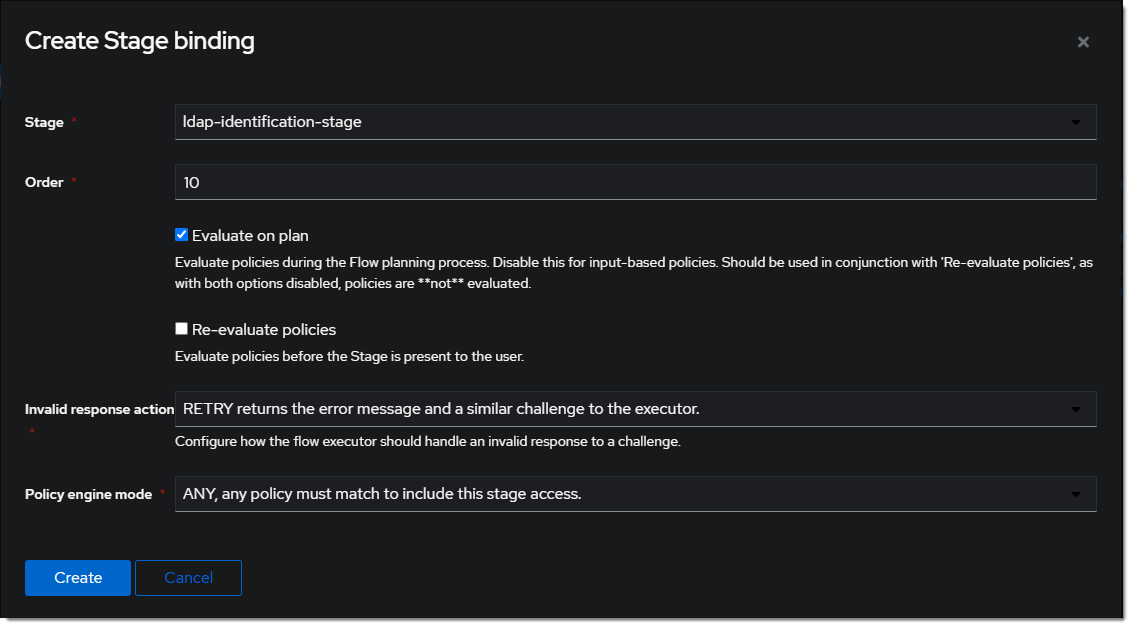
- Click
Bind Stagechooseldap-authentication-loginand set the order to30.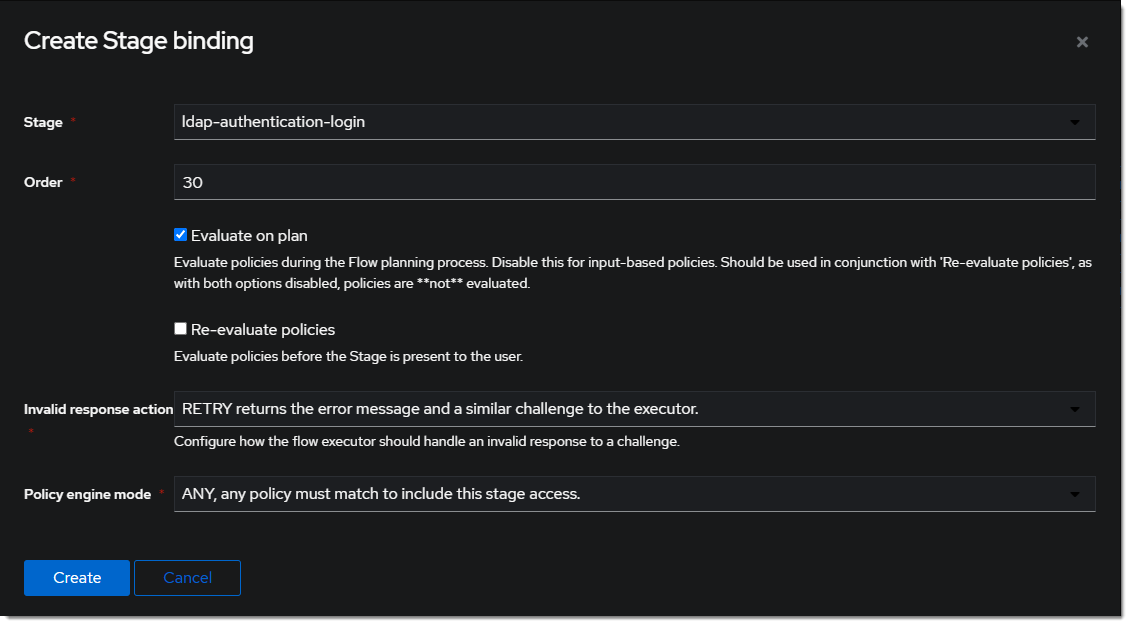
- Edit the
ldap-identification-stage.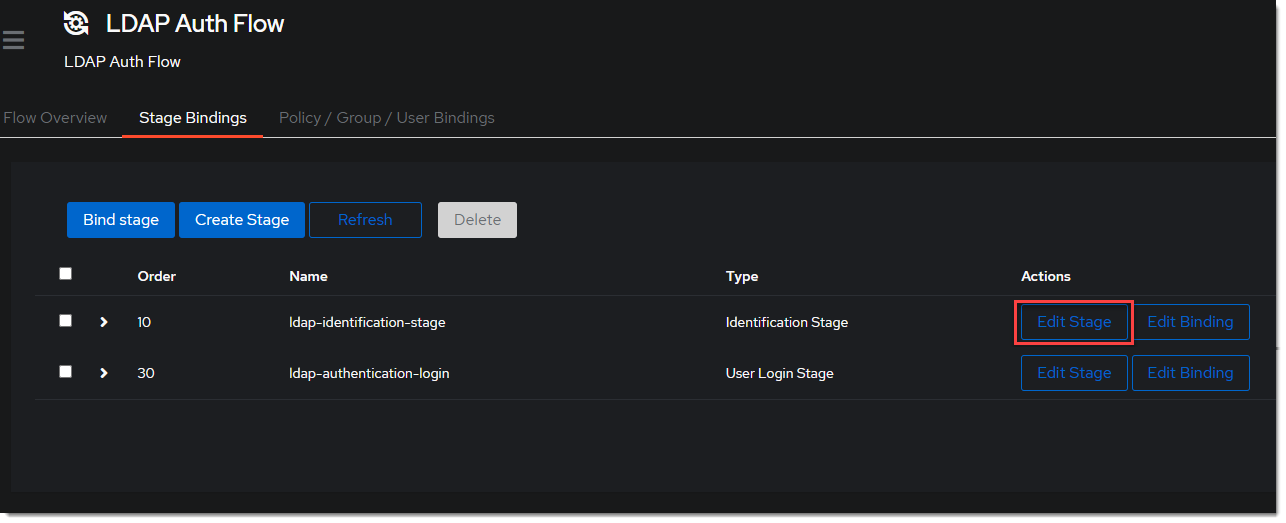
- Change the Password stage to
ldap-authentication-password.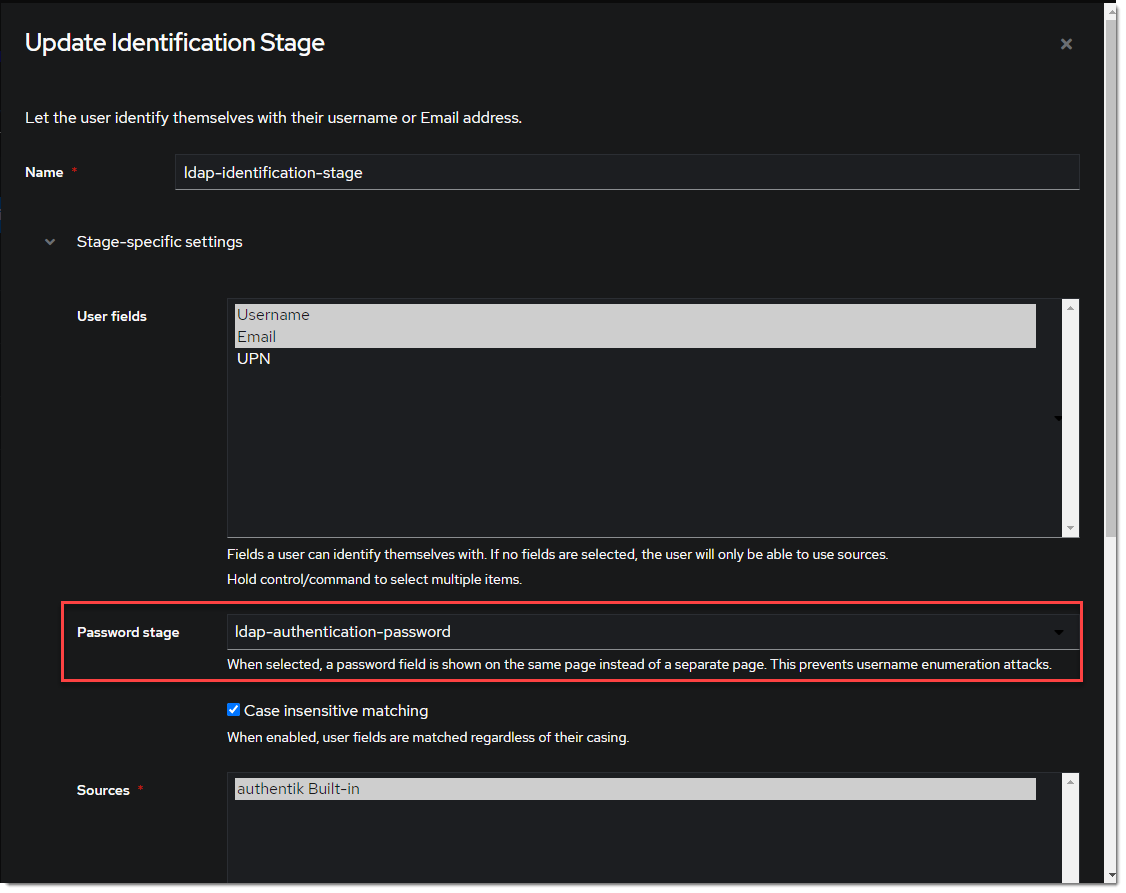
Create LDAP Provider
- Create the LDAP Provider under Applications -> Providers -> Create.

- Name is something meaningful like
LDAP, bind the custom flow created previously (or the default flow, depending on setup) and specify the search group created earlier.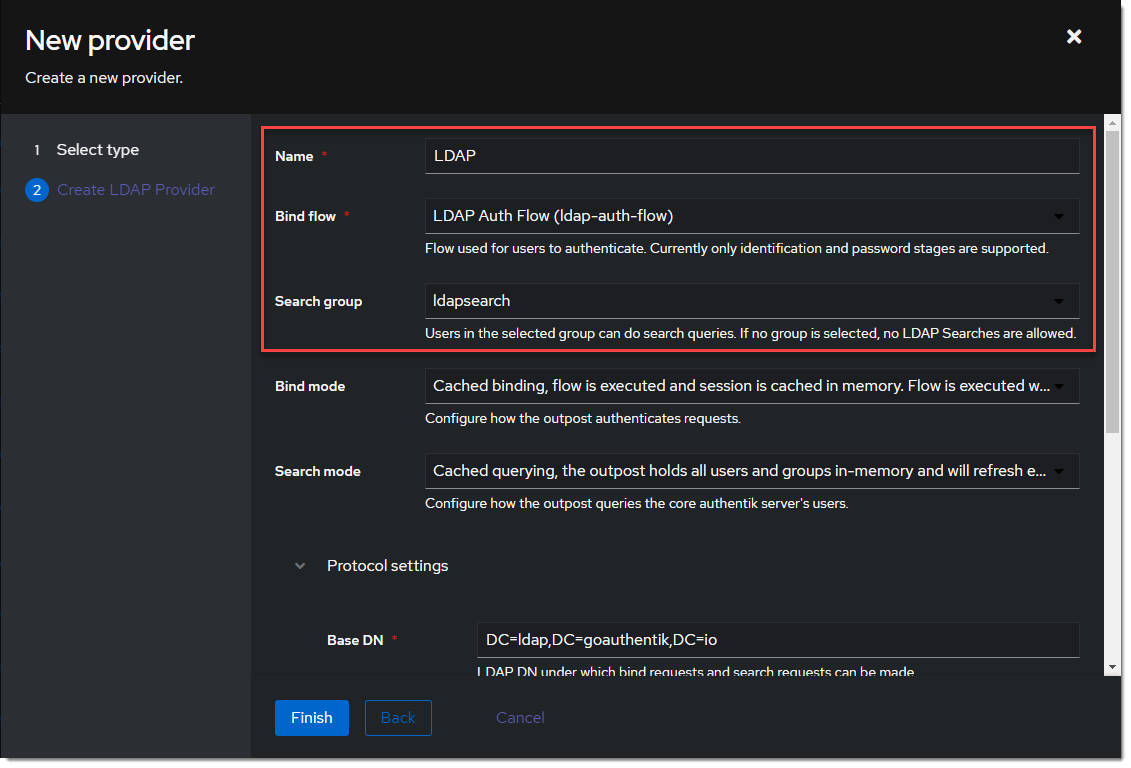
Create LDAP Application
- Create the LDAP Application under Applications -> Applications -> Create and name it something meaningful like
LDAP. Choose the provider created in the previous step.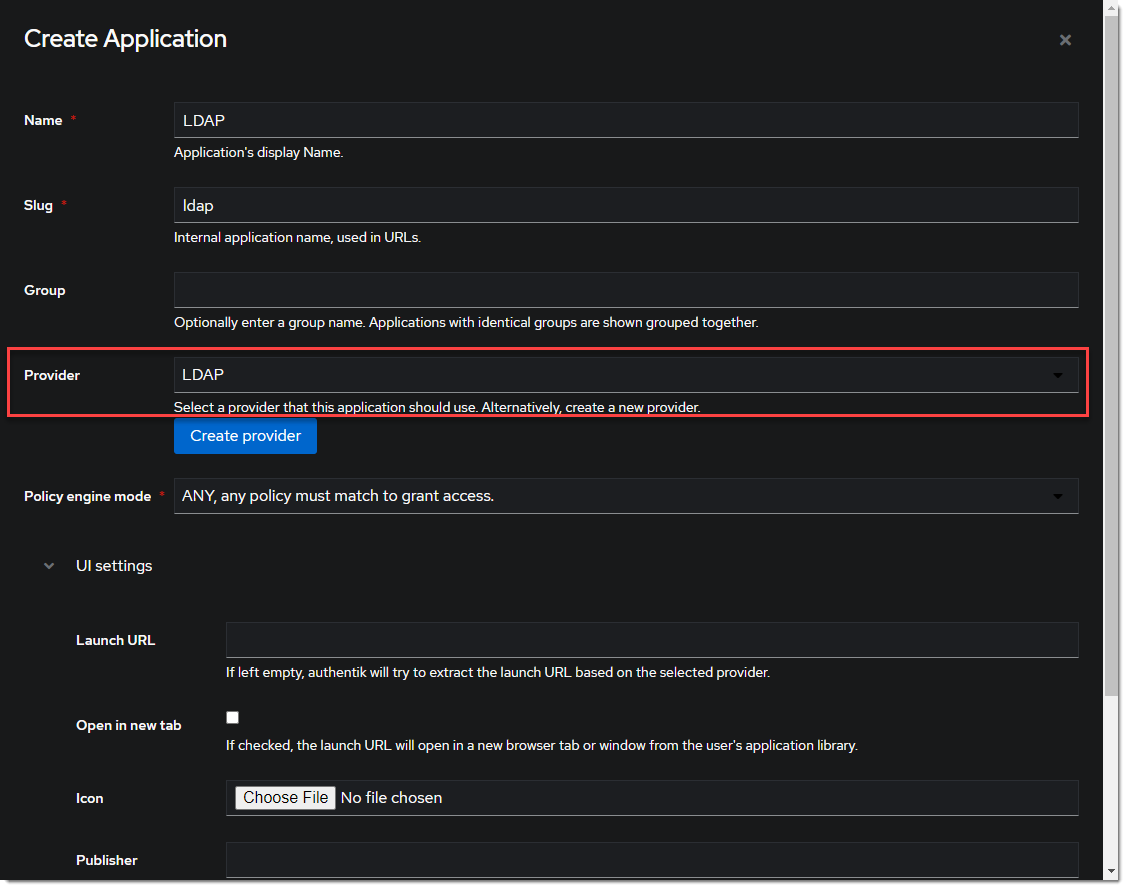
Create LDAP Outpost
- Create (or update) the LDAP Outpost under Applications -> Outposts -> Create. Set the Type to
LDAPand choose theLDAPapplication created in the previous step.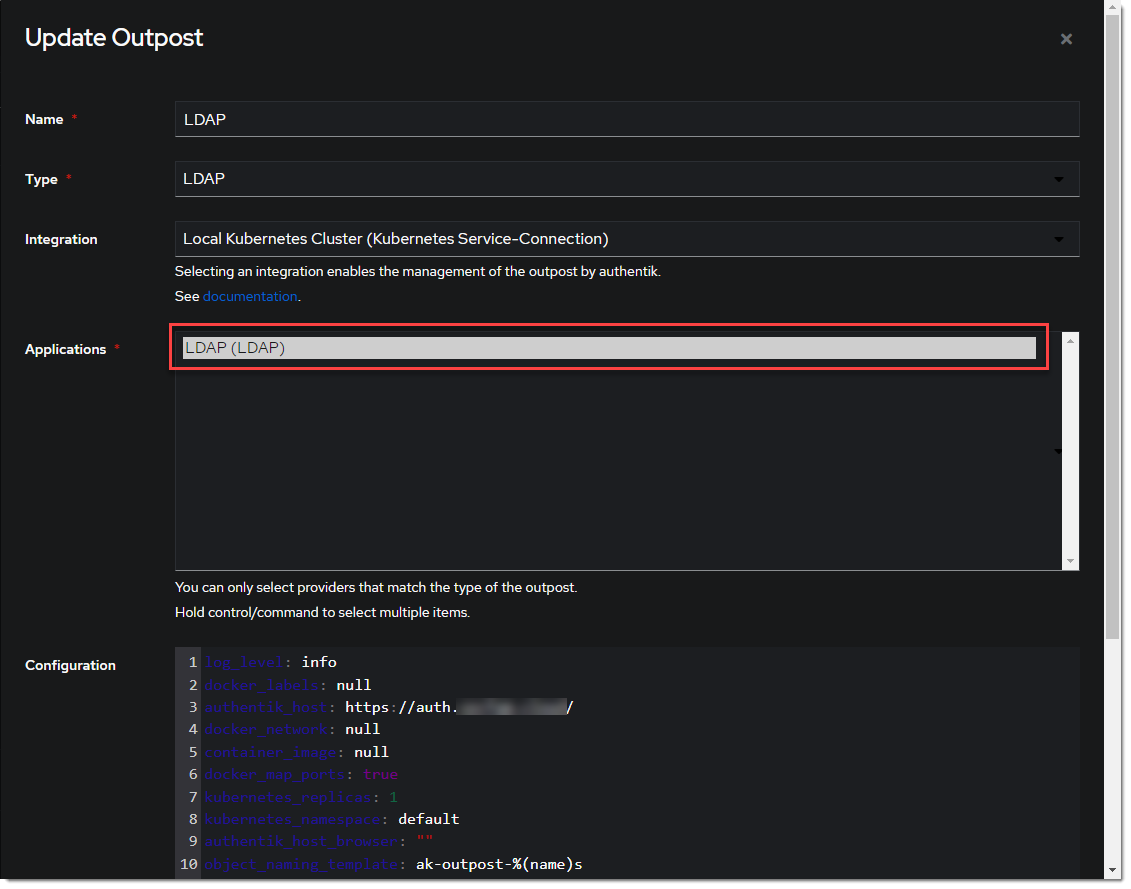
ldapsearch Test
Test connectivity by using ldapsearch.
:::info ldapsearch can be installed on Linux system with these commands
sudo apt-get install ldap-utils -y # Debian-based systems
sudo yum install openldap-clients -y # CentOS-based systems
:::
ldapsearch \
-x \
-h <LDAP Outpost IP address> \
-p 389 \ # Production should use SSL 636
-D 'cn=ldapservice,ou=users,DC=ldap,DC=goauthentik,DC=io' \
-w '<ldapuserpassword>' \
-b 'DC=ldap,DC=goauthentik,DC=io' \
'(objectClass=user)'
:::info This query will log the first successful attempt in an event in the Events -> Logs area, further successful logins from the same user are not logged as they are cached in the outpost. :::